thick client application security testing infosec|thick client applications vulnerabilities : wholesaling The Hybrid Infrastructure on which the Thick Client Application usually resides poses more security challenges than web-based thin clients. To put it in simple terms, the Thick Client Application runs on the user’s system, . webSe você está procurando palpites Brasileirão Série B, você está no lugar certo! Encontre prognósticos de futebol para os mercados de 1x2, mais e menos gols, ambas marcam (BTTS), handicaps, resultado ao intervalo e outros palpites para Brasileirão Série B hoje. Nossa equipe de analistas verificou todos os detalhes deste campeonato e .
{plog:ftitle_list}
WEB27 de set. de 2006 · O que é careta: Pessoa antiga, fora da moda, antiquada. Aquele que sempre segue os padrões antigos, que não arrisca coisas novas e diferentes. Definição; Sinônimos; . Aquele menino está fazendo careta para mim 15. 4 9. Careta Significado de Careta Por João Manoel (SP) em 22-11-2009. Compartilhe no Facebook! Compartilhe .
thick client software
Security assessment of thick client applications. Application security assessments of thin client applications are comparatively easier than thick client application, .In this article, we have set up a lab to practice thick client application . 1. Capturing the request via Echo Mirage. Echo Mirage enables intercepting non-HTTP traffic between the tested thick client and the local or remote server. Intercepting requests using this tool, give insight into what kind . In this article, we have discussed the basics of DLL Hijacking vulnerabilities and how one can find and exploit DLL Hijacking vulnerabilities in DVTA application. In the next .
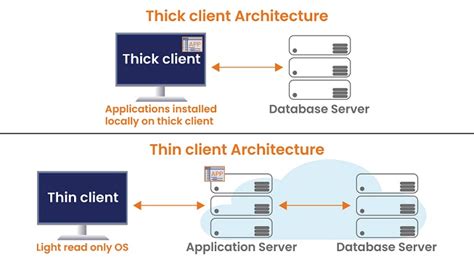
The Hybrid Infrastructure on which the Thick Client Application usually resides poses more security challenges than web-based thin clients. To put it in simple terms, the Thick Client Application runs on the user’s system, . Diagram 1.2 (3) the thick client can be divided into two parts as shown below: (3.1) exe files or (3.2) web-based launcher like a java-based application.This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security. This course uses a modified version of vulnerable Thick Client Application called DVTA to demonstrate how thick client application vulnerabilities can be identified and exploited.
Practical Thick Client Application Penetration Testing using Damn Vulnerable Thick Client App: Insecure Data Storage Background: Welcome to part-3 of thick . Skip to content. 708.689.0131; . SecVulture is an Information Security professional with experience in , Thick client and Mobile Application Security, currently working with Infosec .This process can be done with a running process, or it can run the application on the user's behalf. This type of security testing falls under Thick Client Application Security Testing. Thick Clients Applications can be further divided into two parts: Proxy-aware Thick Clients; Proxy-Unaware Thick ClientsWelcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and practical methodology for thick client Pentesting. Whether you're . Let us test Damn Vulnerable Thick Client Application to see if it is logging any sensitive information into the console. . SecVulture is an Information Security professional with experience in , Thick client and Mobile Application Security, currently working with Infosec Institute as a researcher.
In the rapidly evolving landscape of cybersecurity, organizations face an increasing challenge to secure their software applications and protect sensitive data. Among the arsenal of defense mechanisms, penetration testing, or "pen testing," has emerged as a vital practice to identify and mitigate vulnerabilities. In this article, we delve into the fascinating world of thick . Thick client applications can be developed using Java, .Net, C/C++, etc. A thick client may follow two-tier architecture or three-tier architecture. In two-tier architecture, the thick clients directly access the back-end database via the internet. In . SecVulture is an Information Security professional with experience in , Thick client and Mobile Application Security, currently working with Infosec Institute as a researcher. . Reversing & Decrypting Database Credentials using Damn Vulnerable Thick Client App; Penetration testing steps: How-to guide on pentesting;
Elevate your thick client applications security with our specialized VA/PT audit, specifically designed for the unique security challenges of desktop and standalone applications. . OWASP is the blueprint for testing the web application security controls. It is safe to say that it helps the developers to develop application. Read the blog. Do . SecVulture is an Information Security professional with experience in , Thick client and Mobile Application Security, currently working with Infosec Institute as a researcher. Email: [email protected] . Top 10 Linux distro for ethical hacking and penetration testing; Penetration testing steps: How-to guide on pentesting .
Security testing approach for thick clients. Security testing approaches for thick client applications typically involve conducting penetration tests, vulnerability assessments, code reviews, and security audits to comprehensively evaluate .
Practical Thick Client Application Penetration Testing using Damn Vulnerable Thick Client App: Automated Source code review Background: In the previous arti. Skip to content. 708.689.0131; . SecVulture is an Information Security professional with experience in , Thick client and Mobile Application Security, currently working with Infosec .
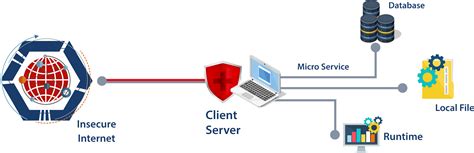
A thick client, also known as a fat client, is a client application that can provide rich functionality, independent of the server in a network. Thick clients can perform the majority of their functions without a live connection to the server.
SecVulture is an Information Security professional with experience in , Thick client and Mobile Application Security, currently working with Infosec Institute as a researcher. Email: [email protected] .Resources for Application Security including , API, Android, iOS and Thick Client Topics android security hacking cybersecurity penetration-testing infosec application-security pentesting bugbounty appsec security-testing . Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. . Effective information gathering lays the foundation for a thorough security assessment, enabling testers to identify and .Discover smart, unique perspectives on Thick Client Security and the topics that matter most to you like Application Security, Cybersecurity, Vapt, Penetration Testing, Infosec, Learning .
Thick client penetration testing focuses on identifying vulnerabilities within client-server applications where the client-side application (thick client) performs significant processing.
thick client security testing
Enhanced Integration Security: Thick Client Penetration Testing at Securityium significantly enhances integration security by accurately examining how thick client applications interact with other systems and services. Our Thick Client Pentesting identifies vulnerabilities in integration points, such as insecure communication channels and .The thick client applications are made of two types: Two tier thick client application: The two-tier thick client application consists of the user computer and the server. In this type, the application is installed on the client side, which directly communicates with the database on the server. These usually involve legacy applications. (E.g.
Shubham Mittal is an information security professional with experience in web appsec, network vapt, mobile security testing, config audits and thick client application testing. In free time, he like to hunt for bugs, and study research papers. Still, some organizations are highly dependent on thick-client applications. Yet, there are no proper security standards for thick-client penetration testing. Hence, it has become more difficult for organizations to identify and eliminate the security flaws in it.Attack surface visibility Improve security posture, prioritize manual testing, free up time. CI-driven scanning More proactive security - find and fix vulnerabilities earlier. Application security testing See how our software enables the world to secure the web. DevSecOps Catch critical bugs; ship more secure software, more quickly. Penetration testing Accelerate penetration . However, the same is not true for thick client applications. We do not have automated tools available for automating the security testing of thick client applications. In my previous article on "Application Security Testing of Thick Client Applications", I mentioned a few tools that can be used for penetration testing of a thick client .
Thick clients are the applications that must be installed on desktops/laptops or servers. These applications can be run on the internet or without the internet. The most common example of a thick client is the installer Skype installed on the desktop/laptop. Other examples of Thick Client are Firefox, Chrome, Microsoft Teams, Zoom, etc. Thin clients.
влагомер опилок фауна пм
The Wizard of Oz Slots online game has a very tempting jackpot and some really fun bonuses on offer. If you’re wondering how to winbig at slots, the jackpot is the symbol to look out for. It’s the most valuable in the whole game as 5 of these could score you a whopping 10,000 free coins. For 4 symbols you would . Ver mais
thick client application security testing infosec|thick client applications vulnerabilities